Table of contents
Introduction
In today's digital landscape, cybersecurity is paramount. With the ever-growing sophistication of cyber threats, organizations need to adopt a proactive approach to safeguarding their systems and sensitive data. One crucial component of this approach is security testing. In this comprehensive guide, we'll delve into the various aspects of security testing, its importance, methodologies, and best practices.
Understanding Security Testing
Definition: Security testing is a crucial process in the field of information technology that involves evaluating and assessing the security features of a system to identify vulnerabilities, potential risks, and weaknesses. It is a proactive approach aimed at ensuring that an application, network, or system is resilient against unauthorized access, data breaches, and other security threats.
Objectives:
Identifying Vulnerabilities: Security testing aims to uncover vulnerabilities within a system that could be exploited by malicious entities. This includes weaknesses in code, configuration, or design.
Risk Assessment: The process involves assessing potential risks associated with the identified vulnerabilities, providing a basis for prioritizing and addressing the most critical issues.
Compliance Assurance: Security testing helps organizations ensure compliance with industry-specific security standards, regulations, and best practices.
Preventing Data Breaches: By identifying and mitigating security flaws, security testing plays a crucial role in preventing unauthorized access and data breaches.
Continuous Improvement: The objective is not only to address current vulnerabilities but also to establish a framework for ongoing security improvements to adapt to evolving threats.
Importance in Today's Cyber Threat Landscape:
In today's rapidly evolving cyber threat landscape, where sophisticated attacks and data breaches are on the rise, security testing holds paramount importance.Key Points:
Protection of Sensitive Data: Organizations handle vast amounts of sensitive data. Security testing helps ensure the protection of this data from theft or unauthorized access.
Reputation Management: A security breach can have severe consequences for an organization's reputation. Regular security testing helps prevent breaches and safeguards the trust of clients and stakeholders.
Legal and Regulatory Compliance: Many industries have stringent data protection regulations. Security testing is essential for compliance with laws such as GDPR, HIPAA, and others.
Financial Implications: The financial repercussions of a security breach can be enormous. Security testing provides a cost-effective way to prevent potential financial losses.
Types of Security Testing:
--> Penetration Testing:

Objectives:
Identifying Weaknesses: Penetration testing aims to uncover vulnerabilities in software, hardware, or network infrastructure that could be exploited by attackers. This includes flaws in code, misconfigurations, or weaknesses in security protocols.
Realistic Simulation: The process involves simulating realistic attack scenarios to understand how an attacker might exploit vulnerabilities. This simulation helps organizations prepare and strengthen their defenses.
Risk Assessment: Penetration testing goes beyond merely finding vulnerabilities; it assesses the potential impact of these vulnerabilities on the organization. It helps in prioritizing and addressing the most critical security issues.
Security Controls Evaluation: Evaluating the effectiveness of existing security controls, such as firewalls, intrusion detection systems, and access controls, is a crucial aspect of penetration testing.
Compliance Verification: Penetration testing helps organizations ensure compliance with industry-specific regulations, standards, and best practices. It provides evidence that security measures meet the required criteria.
Phases of Penetration Testing:
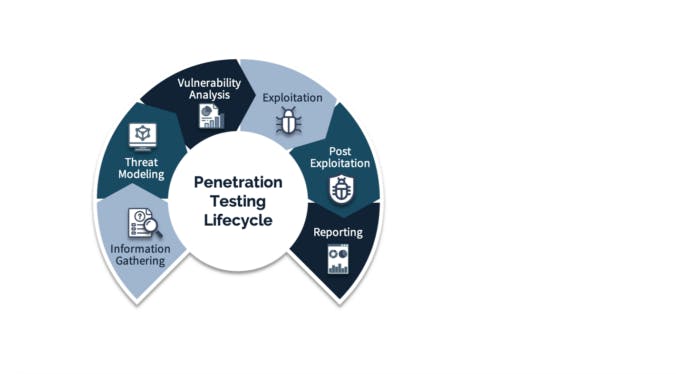
Planning: Defining the scope, goals, and objectives of the penetration test. This phase involves collaboration between the testing team and the organization to ensure a clear understanding of expectations.
Information Gathering: Collecting relevant information about the target, such as IP addresses, domain names, and network infrastructure. This phase may involve passive and active reconnaissance techniques.
Vulnerability Analysis: Identifying and analyzing potential vulnerabilities based on the gathered information. This involves using various tools and manual techniques to assess the target's security posture.
Exploitation: Attempting to exploit identified vulnerabilities to gain unauthorized access or compromise systems. This phase simulates real-world attacks to understand the impact of successful exploitation.
Post-Exploitation: Assessing the extent of compromise and evaluating the ability to maintain access. This phase helps in understanding the potential consequences of a successful attack.
Reporting: Documenting the findings, including identified vulnerabilities, their severity, and recommendations for remediation. A comprehensive report is provided to the organization, detailing the testing process and results.
Benefits of Penetration Testing:
Risk Mitigation: Identifying and addressing vulnerabilities proactively reduces the risk of security breaches and their associated impacts.
Enhanced Security Awareness: Penetration testing helps organizations and their staff understand potential security risks and adopt a security-conscious mindset.
Regulatory Compliance: Meeting compliance requirements by identifying and rectifying security issues that may violate industry or regulatory standards.
Continuous Improvement: Providing valuable insights for ongoing security improvements and adapting defenses to evolving threats.
--> Vulnerability Assessment:
Objectives:
Identification of Vulnerabilities: Vulnerability assessments aim to discover and catalog vulnerabilities within the target system. This includes weaknesses in software, hardware, configurations, or human factors.
Risk Evaluation: Assessing the potential impact and severity of identified vulnerabilities. This involves considering factors such as the likelihood of exploitation and the potential consequences if a vulnerability is exploited.
Prioritization: Prioritizing vulnerabilities based on their severity and potential impact on the organization's operations, data, and overall security. This step helps focus resources on addressing the most critical issues first.
Continuous Monitoring: Implementing continuous monitoring practices to stay abreast of changes in the threat landscape and evolving vulnerabilities that may affect the organization.
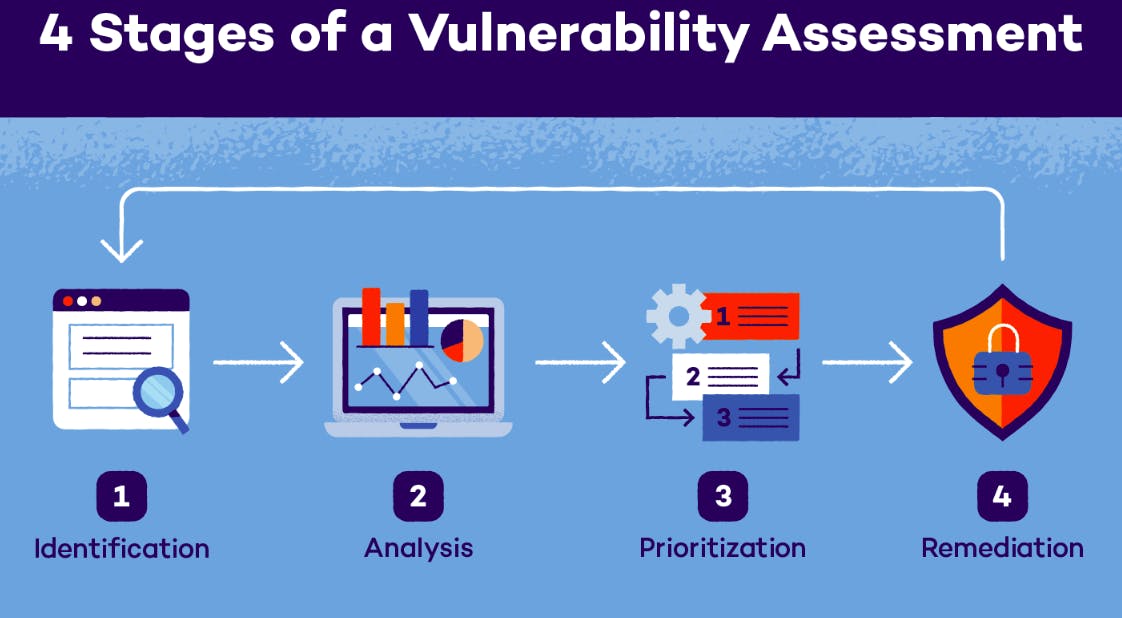
Phases of Vulnerability Assessment:
Pre-Assessment Planning: Defining the scope, goals, and objectives of the vulnerability assessment. Establishing the criteria for success and collaboration with stakeholders.
Asset Identification: Identifying and cataloging assets within the target environment. This includes hardware, software, network devices, and other components.
Vulnerability Scanning: Conducting automated scans using specialized tools to identify known vulnerabilities in the system. This phase may include scanning networks, servers, applications, and databases.
Analysis and Verification: Analyzing the results of vulnerability scans to verify the accuracy of findings and eliminate false positives. This step ensures that the identified vulnerabilities are valid and require attention.
Risk Assessment: Assessing the risk associated with each identified vulnerability. This involves evaluating the likelihood of exploitation and the potential impact on the organization.
Reporting: Compiling a comprehensive report detailing the identified vulnerabilities, their severity levels, and recommendations for remediation. The report serves as a guide for addressing security weaknesses.
Benefits of Vulnerability Assessment:
Early Detection: Identifying vulnerabilities before they can be exploited allows organizations to address issues proactively, minimizing the risk of security breaches.
Resource Prioritization: Enabling organizations to allocate resources efficiently by addressing the most critical vulnerabilities first.
Compliance Assurance: Assisting in meeting regulatory and compliance requirements by identifying and addressing security weaknesses that may violate standards.
Improved Security Posture: Providing insights that contribute to the ongoing improvement of an organization's overall security posture.
Cost-Effective Security: Offering a cost-effective means of identifying and resolving vulnerabilities compared to the potential costs associated with a security breach.
--> Security Auditing:

Objectives:
Policy and Compliance Verification: Ensuring that organizational policies and procedures align with regulatory requirements, industry standards, and internal security guidelines.
Risk Identification: Identifying potential risks and vulnerabilities within the information systems and processes of the organization.
Security Control Assessment: Evaluating the effectiveness of implemented security controls, including firewalls, access controls, encryption, and other protective measures.
Incident Response Evaluation: Assessing the organization's readiness and effectiveness in responding to and mitigating security incidents.
Continuous Improvement: Providing insights and recommendations for ongoing improvement of security measures based on audit findings.
Phases of Security Auditing:
Pre-Audit Planning: Defining the scope, goals, and objectives of the security audit. Establishing criteria for success and collaboration with relevant stakeholders.
Policy Review: Examining and validating organizational policies and procedures to ensure they are comprehensive, up-to-date, and in compliance with relevant standards.
Access Control Evaluation: Assessing the adequacy and effectiveness of access controls, including user permissions, authentication mechanisms, and authorization processes.
Infrastructure Assessment: Evaluating the security of the organization's network infrastructure, including routers, switches, firewalls, and other network devices.
Data Security Analysis: Reviewing the security measures in place to protect sensitive data, including encryption, data backup, and data loss prevention.
Incident Response Testing: Simulating security incidents to evaluate the organization's incident response capabilities and the effectiveness of response procedures.
Documentation and Reporting: Compiling a detailed report that includes audit findings, identified vulnerabilities, areas of compliance, and recommendations for improvement.
Benefits of Security Auditing:
Regulatory Compliance: Ensuring that the organization complies with relevant laws, regulations, and industry standards.
Risk Management: Identifying and addressing security risks helps to minimize the likelihood and impact of security incidents.
Continuous Compliance Monitoring: Establishing a framework for ongoing compliance monitoring and adherence to security policies.
Enhanced Security Awareness: Raising awareness among employees and stakeholders about security best practices and the importance of compliance.
Optimized Security Controls: Providing insights to optimize and strengthen existing security controls for better protection against threats.
--> Security Scanning:

Objectives:
Vulnerability Detection: Identifying and cataloging vulnerabilities within the target system, including software vulnerabilities, misconfigurations, and potential weaknesses in network infrastructure.
Quick and Efficient Assessment: Conducting rapid assessments of the security posture using automated scanning tools to cover a wide range of potential issues.
Continuous Monitoring: Providing continuous monitoring capabilities to detect new vulnerabilities that may emerge over time.
Prioritization of Remediation: Prioritizing identified vulnerabilities based on severity allows organizations to address the most critical issues first.
Phases of Security Scanning:
Pre-Scanning Preparation: Defining the scope and goals of the security scanning process. This involves determining the assets to be scanned, specifying scanning tools, and setting scanning parameters.
Automated Scanning: Employing automated tools to scan the target environment for vulnerabilities. This may include network scanners, web application scanners, and vulnerability scanners.
Analysis of Results: Analyzing the results generated by the scanning tools to verify the accuracy of findings and eliminate false positives. This step ensures that the identified vulnerabilities are valid and require attention.
Risk Assessment: Assessing the risk associated with each identified vulnerability, considering factors such as the likelihood of exploitation and potential impact.
Reporting: Compiling a comprehensive report that includes details of the identified vulnerabilities, their severity levels, and recommendations for remediation.
Benefits of Security Scanning:
Efficiency: Conducting quick and automated assessments allows organizations to efficiently identify vulnerabilities and weaknesses.
Comprehensive Coverage: Scanning tools can cover a wide range of potential security issues, including software vulnerabilities, configuration errors, and network weaknesses.
Continuous Monitoring: Providing a continuous and automated means of monitoring for new vulnerabilities that may arise over time.
Prioritization: Enabling organizations to prioritize remediation efforts based on the severity of identified vulnerabilities.
Cost-Effective Security Assessment: Offering a cost-effective way to perform regular security assessments without the need for extensive manual efforts.
--> API Security Testing:

Objectives:
Authentication and Authorization Verification: Ensuring that APIs require proper authentication and authorization mechanisms to control access to sensitive functions and data.
Data Validation and Integrity: Verifying that input and output data are properly validated to prevent injection attacks and ensure the integrity of data during transmission.
Encryption and Secure Transmission: Evaluating the use of encryption protocols (e.g., HTTPS) to secure data in transit between API clients and servers.
Rate Limiting and Throttling: Testing APIs for appropriate rate limiting and throttling mechanisms to prevent abuse and protect against denial-of-service (DoS) attacks.
Error Handling and Information Leakage Prevention: Assessing how errors are handled by the API to prevent the exposure of sensitive information and ensuring that error messages provide minimal details to potential attackers.
Access Control Mechanisms: Evaluating access control mechanisms within APIs to prevent unauthorized access to sensitive functions, endpoints, or data.
Security Headers Implementation: Verifying the presence and effectiveness of security headers (e.g., Content Security Policy, Strict-Transport-Security) in API responses.
Logging and Monitoring: Ensuring that proper logging is implemented to capture relevant security events and assessing the effectiveness of monitoring systems for detecting and responding to security incidents.
Dependency Analysis: Analyzing and testing third-party dependencies and libraries used by the API for known vulnerabilities.
Compliance Testing: Ensuring that the API complies with relevant security standards, industry regulations, and best practices.
Phases of API Security Testing:
Authentication and Authorization Testing: Verification of the API's authentication and authorization mechanisms, including testing various authentication methods and roles.
Data Validation Testing: Assessment of input validation mechanisms to prevent injection attacks and validation of data integrity during transmission.
Encryption and Transmission Security Testing: Evaluation of the API's use of encryption protocols and verification of secure data transmission practices.
Rate Limiting and Throttling Testing: Testing the API for appropriate rate limiting and throttling to prevent abuse and protect against DoS attacks.
Error Handling and Information Leakage Testing: Assessment of error-handling mechanisms to prevent information leakage and exposure of sensitive data.
Access Control Testing: Verification of access control mechanisms to ensure proper restriction of access to sensitive functions and data.
Security Headers Testing: Evaluation of the presence and effectiveness of security headers in API responses.
Logging and Monitoring Testing: Assessment of logging mechanisms to capture security events and testing the effectiveness of monitoring systems.
Dependency Analysis and Testing: Analysis and testing of third-party dependencies and libraries for known vulnerabilities.
Compliance Testing: Verification of the API's compliance with relevant security standards, industry regulations, and best practices.
Benefits of API Security Testing:
Data Protection:
Ensuring the protection of sensitive data transmitted and processed through APIs.
Prevention of Unauthorized Access:
Mitigating the risk of unauthorized access to API endpoints and functions.
Compliance Assurance:
Ensuring that APIs adhere to regulatory requirements and industry security standards.
Threat Mitigation:
Identifying and mitigating potential security threats before they can be exploited.
Secure Integration:
Facilitating secure integration between different software components.
Next: Chapter 2